BurninCandle Writeup| IcedID Malware
A detailed malware analysis of the IcedID infection leading to Cobalt Strike using packet capture (PCAP) investigation.
Hi all, I’m back again with another Malware Analysis Writeup!!
Challenge Link—https://www.malware-traffic-analysis.net/2022/03/21/index3.html
Scenario
LAN segment data:
- LAN segment range: 10.0.19[.]0/24 (10.0.19[.]0 through 10.0.19[.]255)
- Domain: burnincandle[.]com
- Domain controller: 10.0.19[.]9 — BURNINCANDLE-DC
- LAN segment gateway: 10.0.19[.]1
- LAN segment broadcast address: 10.0.19[.]255
Task : Write an incident report based on the pcap. The incident report should contains 3 sections:
- Executive Summary: State in simple, direct terms what happened (when, who, what).
- Details: Details of the victim (hostname, IP address, MAC address, Windows user account name).
- Indicators of Compromise (IOCs): IP addresses, domains and URLs associated with the infection. SHA256 hashes if any malware binaries can be extracted from the pcap.
Let’s Start!!
To figure out the Details part,
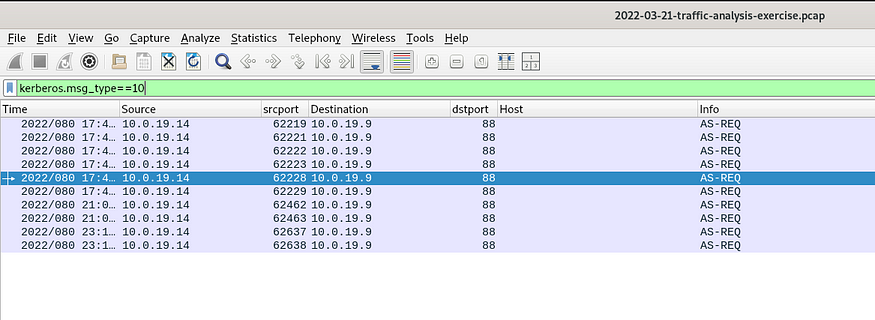
I decided to filter out kerberos packets and particularly the ones with AS-REQ , by using
kerberos.msg_type eq 10
Filtering out AS-REQ Packets
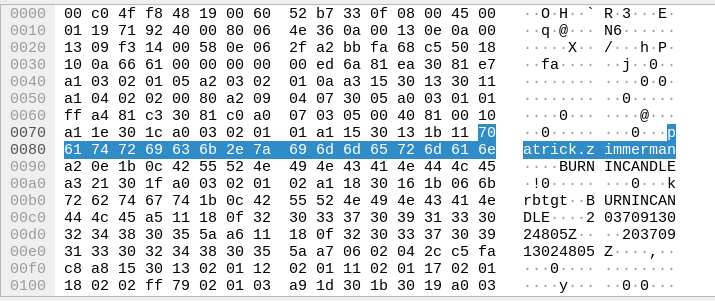
Checking all the packets present there, we are able to figure out the names of Users and Devices.
Name of the User
Name of the Device
Figuring out the Source Address
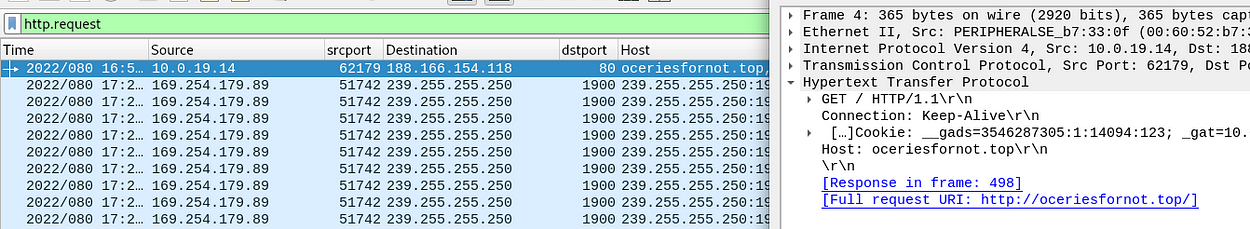
Decided to just see the requests made by using
http.request
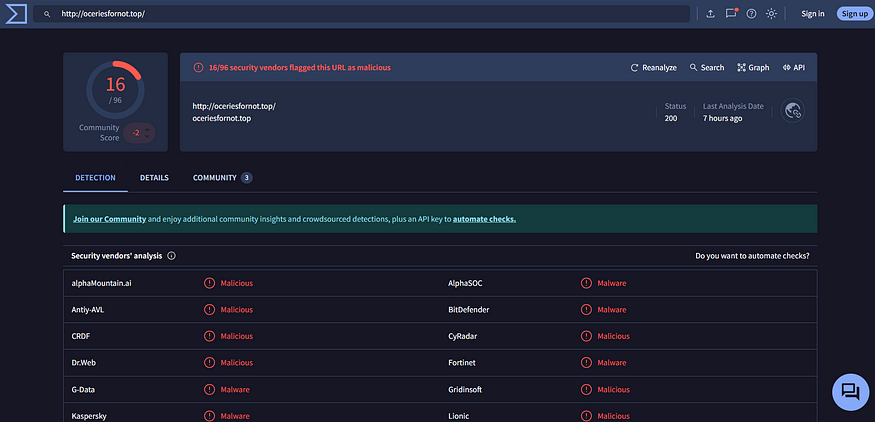
Examining the URL (https://oceriesfornot.top/) in VirusTotal,
Virustotal findings
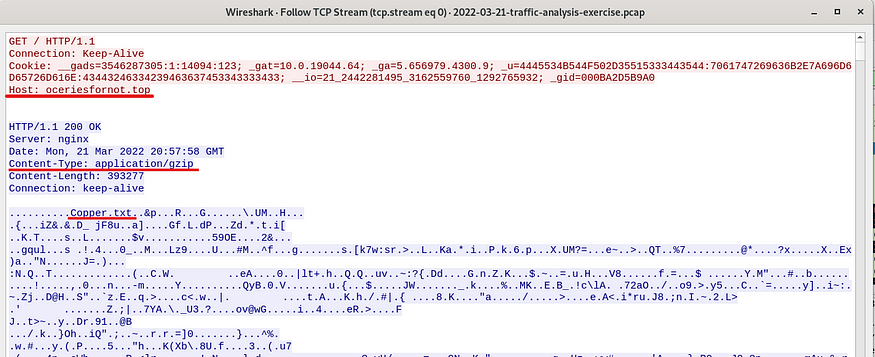
Decided to follow the TCP stream to check if anything can be revealed…
TCP Stream data
Was fascinated by the “cookie” part, so checked what each of them meant…
Notable cookies:
**_gads**: Google Ads tracking.
**_ga**and**_gid**: Google Analytics for user tracking.
**_gat**: Limits requests to Google’s servers.
**_u**and**_io**: Custom session/user identifiers.
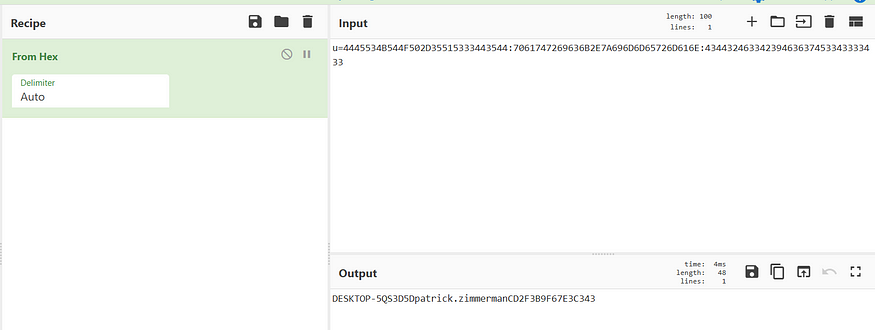
Since _u meant ‘user’ and the info associated with it looked hex-encrypted, I decided to use cyberchef.io to decrypt the info.
Using Cyberchef to decrypt the encoded text
And voila!! We have the complete information of the data.
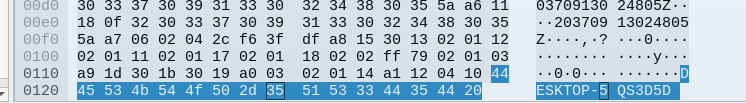
DESKTOP-5QS3D5Dpatrick.zimmermanCD2F3B9F67E3C343
So, this confirms that our analyses related to the details were accurate.
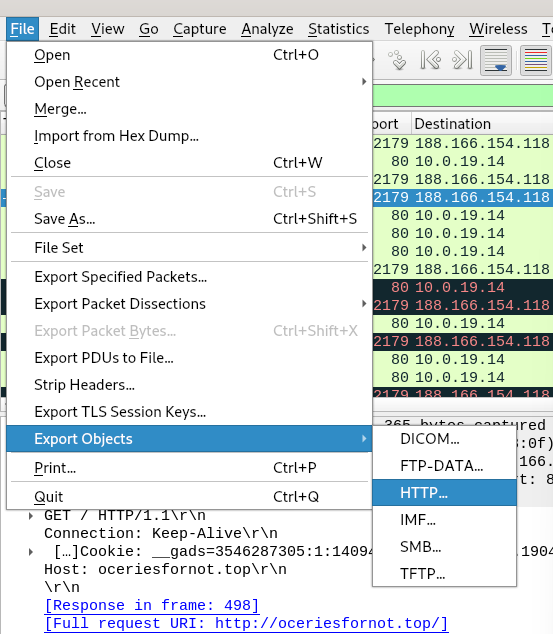
Now I decided to export the documents associated with the packet.
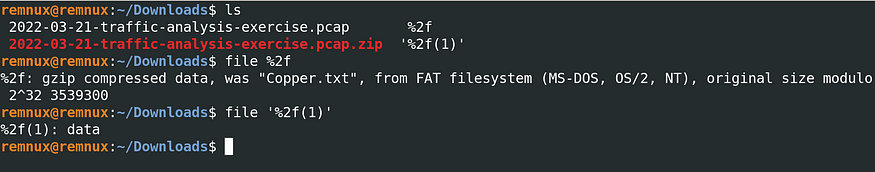
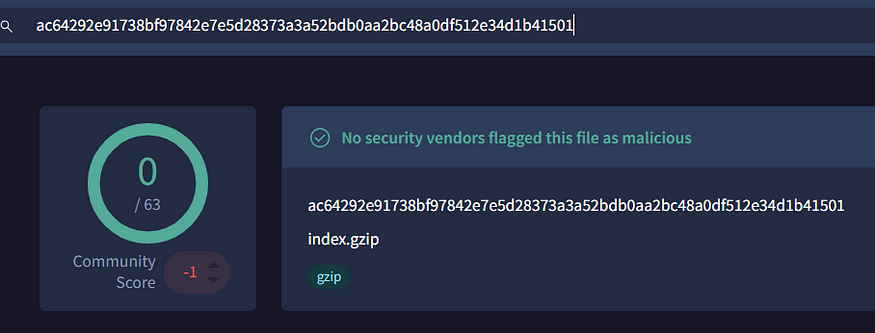
Analyzing the files, we find that the gzip file is called “Copper.txt”, which is…let’s just say…HIGHLY UNUSUAL.
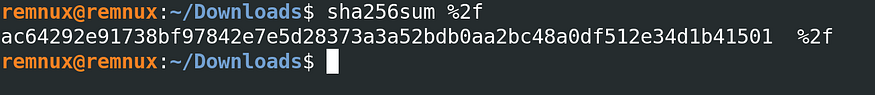
I decided to check the file hash with some security vendors like VirusTotal,
aaaanddd….
WOW. Not Malicious?? Maybe it was a false alarm, or I fell into a trap.
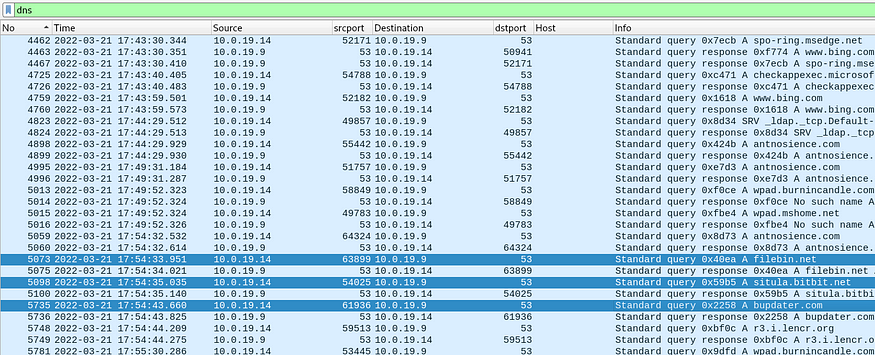
I decided to filter for DNS traffic in wireshark, as DNS traffic can reveal what domains and IP addresses threat actors are using to conduct their malicious activities.
And boom!! Noticed something off.
The websites filebin.net and situla.bitbit.net were visited briefly, with each connection lasting less than 10 seconds. This could mean 2 things:
- Data was being stolen, or
- The malware was downloading more files to harm the system.
But we aren’t sure yet. It is unclear right now.
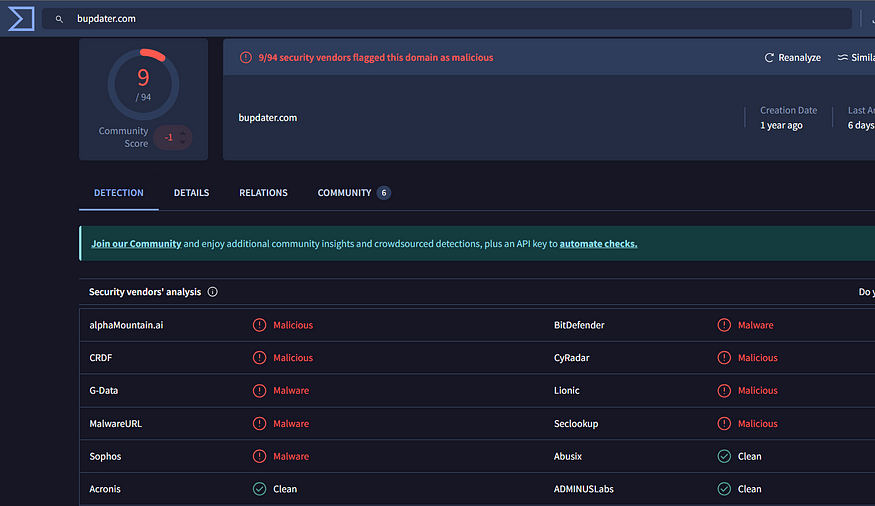
I checked the sites on VirusTotal,
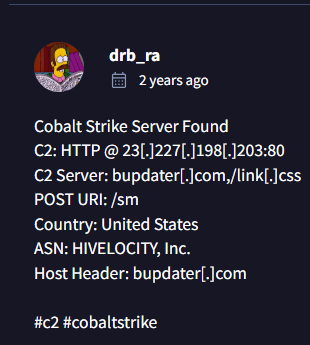
Checking the Community Tab,
A user drb_ra has given everything related to this. Analysis of this data indicates that the server is flagged as a Cobalt Strike Command-and-Control (C2) server.
And yeahhh, it seems like I finally got what’s the problem here.
Upon further research, I found out that a malware type IcedID uses this technique as the first stage loading mechanism (Check out this amazing website — https://www.binarydefense.com/resources/blog/icedid-gziploader-analysis/)
IcedID , CobaltStrike — we’re getting somewhere…..I think I can wrap it off by the analyis here. Here goes the answer:
_______________________________________________________________
Answer for the Problem:
A Windows host (DESKTOP-5QS3D5D) used by Patrick Zimmerman was infected with IcedID malware that led to Cobalt Strike.
Domains for the IcedID malware:
oceriesfornot.top , antnosience.com , suncoastpinball.com
Domains where suspicious traffic was detected:
filebin.net , situla.bitbit.net
Domain where Cobalt Strike happened:
bupdater.com
_______________________________________________________________
Do follow me for more Malware and Packet Analysis blogs!!
Signing off, RDT.